Introduction
In the process of constantly updating the list of modern threats in the information space, the term “Spammm6178” has become one of the focuses of attention of cybersecurity specialists and various communities. The goal of this article is to give a reader a clear vision of what kind of phenomenon “Spammm6178” is, where it began, how it differs from other types of spam, and why spam is a concern in today’s world. In exploring these aspects we attempt to provide a reference greater than coverage seen and enable our readers be informed and safe.
What is “Spammm6178”?
This implies that ‘Spammm6178’ may be a brand, name or alias used in identifying a certain sort of spam incidence. Though the exact roots are not very clear, the popularity of the term has been seen in several forums and discussions, especially the ones related to cyber activities. It may be described as a separate type of spam or way of sending spam messages that has its peculiarities and features that distinguish it from other types of spam.
Origin of the Term “Spammm6178”
The definite history of the irrelevant username of “Spammm6178” is still unclear but it can be traced back to Googling spam techniques. The term may have been derived from a certain spammer’s nick name or a specific code connected to a certain spam campaign. It is important to have an initial appreciation of what it is in order to map its evolvement and recognise the differentiation.
Popularity and Usage in Online Communities
Thus, in multiple online forums, “Spammm6178” is mentioned as a specific type of spamming approach. Again this may be due to the functionality of the site, or its notoriety in some social networking sites. Therefore, an observation of the application of the term in such forums will help in understanding why it has subject of discussion and research.
Historical Background and Evolution of Spam

Spam too has history and traced its origin to the early days of the Interne Due to this understanding, it offers background information about why terms such as ‘Spammm6178’ appears and how it falls in the roll out of spam.
Early Instances of Spam on the Internet
‘Spam’ was first noticed in the 1970s, when people, who were connected in the ARPANET network, sent unwanted messages to others. Such early instances was mostly regarded as mere nuisance but harbingered the more elaborate spam strategies present today.
Evolution of Spam Tactics Over Time
Spam techniques have not remained stagnant, but they have escalated from mere old school con jobs in emails to an entirely new level of phishing. All the novelties introduced impose the task of going around spam controls with higher efficiency of spam-related campaigns.
The Mechanics of Spamming: How Does It Work?
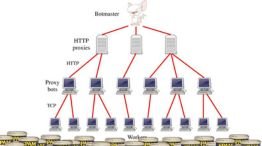
Spamming encompasses different techniques and instruments allowing to spread the unwanted messages or advertisements to the targeted or non-targeted population. These methods remain dynamic in order to avoid being discovered as well as remaining useful.
Common Methods and Techniques Used in Spam
- Bulk Email Campaigns: Vehicle for conveying a huge amount of emails that contain only an advertising or a phishing message.
- Botnets: Computerized networks of affected gadgets are utilized to deliver spam messages in vast quantities.
- Social Engineering Tactics: These are messages to try and make the recipient give out personal details or click on sinister links.
Tools and Software Used for Spamming
Spammers employ the services of a number of tools and applications to conduct spams for them. Such tools may range from the plain script all the way to complex applications which are programmed to emulate human conduct in a bid to avoid being noticed.
Different Types of Spam
This is a brief look at the different types of spam and how they operate and who they are aimed at.
Email Spam
It is however important to note that email spam is amongst the most recognized forms of spam. It is the act of sending messages to numerous users randomly, and in most cases; these messages contain advertisements or attempts to access users’ personal information.
Social Media Spam
Social media spam is regarded as fake profiles, bot-driven comments and messages with the objective of influencing social media algorithms or pimping content.
Comment Spam on Blogs and Websites
Blog and forums comment spam can be seen in many sites where spammers only post comments irrelevant to the blog or topics being discussed but just post such comments for the sake of the link that goes back to their site or simply to post links that would take the site visitors to other sites.
SMS and Messaging App Spam
When smartphones and other such devices have become popular, spammers have started sending unwanted texts and links to the SMS and other messaging apps.
Why “Spammm6178” is a Unique Phenomenon
‘Spammm6178’ is in a way or the other different because it has distinctive features that make it different from other spam methods.
Distinct Characteristics of “Spammm6178”
Some distinctions may be in terms of delivery techniques, targeting methods or the content of such messages that has given them certain notoriety and effectiveness. It is important to understand these characteristics so as to get a feel of how it affects and or presents a challenge.
Community Perception and Reactions
The reactions over “Spammm6178” may be different in the groups and communities in the social network. For some, it may be a very serious thing while to others it may just be an irritation. Nevertheless its existence is universal which underlines the necessity of efficient measures that may be taken against it.
The Impact of Spam on Individuals and Organizations

Spam goes far beyond mere clogging the in boxes within computers; it can cause havoc on the security of an individual or organization and also on reputation.
Personal Data Security Risks
Many spam messages’ goals are to mislead the recipient and provide the spammer with a core of individual data for identity theft or money-related frauds. Personal information must be protected from such threats, and one has to be alert all the time.
Financial Implications of Spam
Currently organizations may experience reduced efficiency, quantitative and qualitative losses due to fraud, as well as face expenses linked with anti spam measures. To minimize such financial effects, efficient spam management solution has always been emphasized.
Damage to Reputation and Credibility
Linking an organization to spam whether by spamming through other accounts or poor acceptable business email usage is detrimental to an organizations reputation. Paying attention to what has been mentioned above and applying good practices and wachtnes to spam related matters is crucial to reputation.
Legal Aspects of Spamming
There are several regulations made and implemented to fight against spam and punish the culprits but at the same time, it is not an easy task.
Anti-Spam Laws and Regulations Globally
Most of the nations have passed laws like the CAN-SPAM of the USA and GDPR of Europe to control spam and to guard the privacy of the commodity. It is important to note that these regulations have been established with an aim of reducing the amount of spam presently in circulation and to also ensure that spammers are punished for spamming.
Consequences for Spammers
Possible sanctions for spamming are fines, legal prosecution and in some cases even criminal prosecution. The outcomes are typically influenced by the impact of the spam campaign and the intentions of the spammers.
How to Identify and Recognize Spam
Recognizing spam is essential for safeguarding your personal information and maintaining online security.
Red Flags and Warning Signs
Typical characteristics of spam are unknown senders,-links and,uses expressions such as ‘reply now’ or ‘you are in danger’. It is possible to notice these signs in order to alert oneself about possibly spam messages.
Common Traits of Spam Messages
Some of the features evident in spam include; poor grammars, unfamiliar attachment, and an allure that is almost absurd. Knowing these traits relieves one of the burden of determining which is spam and which isn’t.
Effective Strategies to Protect Against Spam
It is possible to protect yourself from spam related issues in the following ways:
Email Filtering Techniques
One can eliminate a lot of unnecessary junk by applying strict filters with improved recognizing algorithms and labeling spam mails. Another issue that spam might use to its advantage is the fact that filters can become antiquated; thus, changing them periodically is a good way to counter these new strategies by spammers.
Social Media Privacy Settings
It’s important to configure display settings on accounts on social networks in order to avoid spam messages and input private data. It is recommended to check and modify such settings from time to time.
Safe Browsing Habits
This must be avoided at all times especially when it comes to clicking links and downloading attachments because it is usually a ground for spam related threats. Specifically, good browsing practices are useful in reducing incidents of spam encounters.
The Role of Technology in Combating Spam

Anti-spam measures are implemented through a number of complex technologies that deal successfully with spam identification.
Machine Learning and AI in Spam Detection
By using machine learning techniques it is easier to analyze the patterns of spam messages compared to those that are actual and necessary, thereby enhancing the accurately of the detection filters. AI-based mechanisms can alter their strategies in response to changes in spam strategies and therefore improve overall efficiency.
Advanced Spam Filtering Algorithms
As to spam filters, these algorithms employ heuristic Continue and big data to learn and improve with new spam strategies, which make them progressively more efficient. It is useful to adopt such state-of-the-art technologies into concepts of spam combating.
Case Studies: Notable Instances of Spamming
Information gained from previous experiences based on the spam events is important in understanding the conduct of the spammers and the effects that they exhibit.
High-Profile Spam Campaigns
Comparing examples of well-known spam campaigns can best explain the actions carried out by spamers and the success, which these measures achieve. These case studies are valuable sources of learning how to respond and prevent such threats.
Impact and Response to Major Spam Attacks
The review of the aftermath of grand spam attacks gives an insight of the impact of a proper spam combating measures. This means that one can learn from responses given in previous similar attacks in form of guidance for future encounters.
The Future of Spam and Cybersecurity
Thus, with the progress of technology, spam also changes form, so it remains a relatively pertinent problem and will have to be fought constantly.
Emerging Trends in Spamming Tactics
Some of the new trends of spam include messages that are now personalized and use artificial intelligence to create realistic messages. It is therefore important to make sure that one keeps abreast with these trends with regards to spam management.
Advancements in Anti-Spam Technologies
Advancements in the cryptography products and service systems Calendar intend to outcompete spammers and safeguard people better. Adopting these advancements can add on the general prevention on spam.
Common Myths and Misconceptions About Spam
Addressing misconceptions about spam can lead to more effective protection strategies.
Debunking Myths Around “Spammm6178”
It is possible to counter some of the myths associated with “Spammm6178” to ensure that people are well informed instead of having misconceptions. It becomes critical to prevent them to know the full outlook of this spam type.
Facts Everyone Should Know
Therefore, presenting the information about spam and about “Spammm6178” can help people be more protected. This has the potential to make or mar the fight against spam and therefore calls for accuracy of information.
Frequently Asked Questions About Spam
Q1: What Sets “Spammm6178” Apart from Other Spam Types?
“Spammm6178” may have distinct features, such as targeted strategies or innovative techniques, that make it different from other forms of spam.
Q2: Is It Possible to Completely Eliminate Spam?
While completely eradicating spam is unlikely, continuous advancements in technology and enforcement efforts aim to significantly reduce its occurrence.
Q3: What’s the Best Way to Report Spam?
Reporting spam to the appropriate authorities and service providers can help limit its spread and impact. Using available reporting tools and services is an effective strategy for tackling spam.
Conclusion
Summarizing Key Points About “Spammm6178”
The case of ‘spammm6178’ is a particular type of spam with the focus in a cyberspace environment, and its analysis demonstrates that the problem of spam remains persistent. That is why, their peculiarities and outcomes should be understood in order to manage them properly.
Final Thoughts on Managing Spam Effectively
At the same time, it should be possible to have effective spam management and protection methods, which in turn are the result of unerring vigilance, the application of technologies, and readily available knowledge of such threats. This way, the challenges relating to spam can be met with the adequate sense of caution by both the individuals and the organizations.
